Under Siege: Real Cybersecurity Horror Stories & How to Prevent Them
A ransomware attack locked tenants out of a commercial office building for three days. Four major tenants cited the incident when they didn't renew their leases. The financial hit? Over $2 million in losses and litigation. This happened to a real building, and stories like it are becoming common enough that savvy tenants now ask about OT security before signing leases.
These stories—and practical solutions—came from a recent NexusCon session where building owners, consultants, and technology providers gathered to talk about what's actually happening in the field. The news isn't all bad. Lendlease successfully secured 19 buildings covering 1.1 million square feet in under six months. Actimeta has developed frameworks for triaging thousands of vulnerabilities into manageable priorities. And multiple owners shared practical steps that work without requiring unlimited budgets or armies of cybersecurity experts.
This article covers both the horror stories and the playbook for fixing them.
The Wake-Up Call: When Smart Buildings Get Dumb
It's 4 a.m. The first office worker arrives at the building entrance. The door won't unlock. By 6 a.m., there's a line stretching down the block.
The access control system has been ransomwared.
The property management company gets the emergency call around 6:30. By 9 a.m., the building owner is staring at an impossible choice: pay $7,200 in Bitcoin to criminals, or pay $65,000 to their vendor—plus burn countless staff hours—rebuilding the system from scratch.
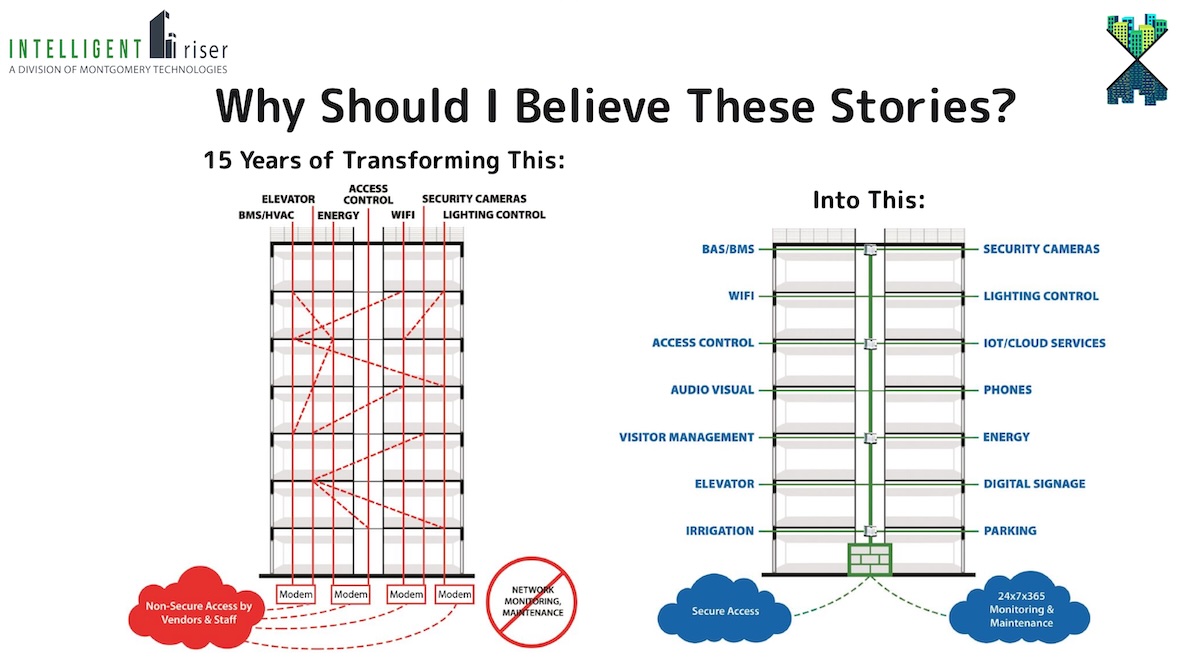
This story comes from Joe Gaspardone, COO at Montgomery Technologies, who's spent 15 years turning tangled building networks into secure, organized systems. He's seen this scenario play out multiple times. The access control incident? Four major tenants left when their leases ended, and they specifically mentioned the hack as a reason they didn't renew.

Worse stories exist. An air-gapped BMS—supposedly unhackable because it had no internet connection—got infected when an engineer plugged in a thumb drive. No internet meant no alerts. The malware spread to every controller, burrowing into device firmware. Cost to fix: $200,000 to rip out, replace, and restore. Plus significant rent credits to tenants who suffered through days of comfort issues.
Elevators have been ransomwared. Multiple times.
Lobby directories have displayed pornography until someone physically disconnected them. Cost to remediate: $7,400.
Security cameras got quietly hacked and accessed for months. Two cases of identity theft followed. Eventually the system got ransomwared too: pay $19,700 in Bitcoin or $180,000 to the vendor.
Building systems aren't theoretical targets anymore. They're getting hit. And the old assumptions about being protected—air gaps, obscurity, 'we're too small to matter'—no longer hold.
The Hidden Cost of Convenience
Your HVAC contractor needs remote access to troubleshoot a problem at 11 p.m. Your elevator vendor needs to push a software update. Your tenant wants seamless badge access integrated with their corporate systems.
Every reasonable request opens a door.
The habits that keep buildings running—port forwarding to let vendors in, shared login credentials, default passwords nobody bothered changing—create exposure. Port forwarding is particularly dangerous. It punches a hole through your firewall, creating a direct pathway from the internet to your building systems.
Michael MacMahon, an OT security consultant at Newcomb & Boyd, has watched this pattern repeat: "There's too much trust in this industry. Everyone assumes someone else has it handled. Nobody does."
Here's a test: Who manages the cameras in your building? Who owns the Wi-Fi in your amenity spaces? Who's accountable when the BMS vendor's laptop brings in malware?
In most buildings, the answers are unclear. IT assumes facilities is handling it. Facilities assumes IT has it covered. Vendors assume the owner is managing security. Joe Aamidor, who consults with owners on building technology strategy, describes the result: "The awareness starts at the board, and they think it's covered—until they realize no one actually owns OT."
One building found out their amenity Wi-Fi was being used for illegal activity when the ISP flagged them. Then the FBI sent a letter: "As the owner of this IP address, you may be liable." The activity involved child trafficking. Nobody had set up even basic security on the network because nobody thought it was their job.
Convenience isn't free. It trades security for efficiency. The problem is that most building owners don't realize they're making that trade until something breaks.
The Myth of "We're Covered"
"Our IT team handles that."
This might be the most dangerous sentence in commercial real estate.
Building systems—HVAC, elevators, access control, lighting—usually sit outside IT's visibility. They're managed by facilities staff or vendors. They run on separate networks. They use protocols IT staff don't understand. And IT security tools often can't even see them, let alone protect them.
Picture a typical building:
- HVAC: Managed by a mechanical contractor with their own remote access
- Access control: Run by a security vendor on a separate network
- Elevators: Maintained by an elevator company using proprietary systems
- Cameras: Operated by yet another vendor
Each system has different remote access methods. Each vendor follows different security practices—or none. Each connection is a potential entry point.
Research from Claroty found that 78% of organizations have separate OT and IT security teams that don't coordinate well. The blind spots this creates are significant.
What gets lost in this fragmentation is accountability. Who's responsible when something goes wrong? Who should be tracking vulnerabilities? Who decides what level of risk is acceptable?
Those questions matter more than any security tool you can buy. Until you answer them, you're just adding more technology to an already confusing mess.
A Real Fix: The Lendlease OT Cyber Journey
When Lendlease decided to address OT cybersecurity across their portfolio, they didn't start with a massive audit that would identify thousands of vulnerabilities. They started with the most exposed point: remote access.
Tom Balme, who leads building technology strategy for Lendlease's investment portfolio, explains the thinking: "An audit will tell you to secure your internet-facing systems first—so don't wait to be told. Start there."
Lendlease developed a phased approach aligned with the NIST Cybersecurity Framework:
Phase 1 (FY25): Protect — Implement secure remote access across the portfolio
Phase 2 (FY26): Identify — Conduct OT audits and deploy asset discovery and vulnerability assessment tools
Phase 3 (FY27): Detect, Respond, Recover — Add monitoring, incident response capabilities, and backup systems

Why start with protection rather than identification? Because it delivers the fastest risk reduction. Securing remote access immediately closes the most common attack vector—without requiring a lengthy audit process or remediation of thousands of vulnerabilities.
The results speak for themselves:
- 19 buildings secured in less than six months
- 125 OT systems protected
- 770+ users onboarded (a mix of facilities staff, contractors, and tenants)
- Immediate cyber uplift delivered
Perhaps most importantly, the project eliminated legacy VPNs and port forwarding—the swiss cheese in most building networks—and gave Lendlease visibility and control over who accesses their OT environments.
Cory Clarke, CPO at Neeve (the platform Lendlease used), notes that the approach allowed rapid deployment: "Simple setup meant the team could start deploying within weeks. Self-service web-based remote access made it practical at scale."
One of the bigger challenges? Tenants. Of the 770+ users onboarded, 355 were tenants who needed access to systems they'd installed in their leased spaces. Getting tenant buy-in and managing their access required clear communication about why the changes mattered and how the new system would work.

Another challenge: port forwarding. Many vendors had grown accustomed to this convenient but dangerous practice. Balancing security requirements with vendor pushback on changing established workflows required patience and clear explanation of the risks.
But the biggest lesson? Starting small and showing results unlocked funding and board buy-in. By proving value quickly, Lendlease secured investment for the next phases of their program.
Tom Balme's advice for other owners: "Start with one building. Prove the value. Scale from there."
Designing for Security: Don't Bolt It On Later
One of the most expensive mistakes building owners make is treating cybersecurity as an afterthought. The conversation between Osman Saleem, Principal Consultant at Actimeta, and Michael MacMahon during the NexusCon session highlighted a critical disconnect: construction teams and operations teams rarely talk to each other during the design phase.
"The hardest part is that construction and operations teams never talk—the facility group inherits the mess," MacMahon explained.
When cybersecurity isn't embedded in design standards and procurement specifications, the cost and complexity of retrofitting security controls later multiplies. Consider these common scenarios:
- Default passwords: Systems ship with factory defaults that never get changed
- Flat networks: All building systems share a single network with no segmentation
- No patching protocols: Contracts don't specify who's responsible for software updates or how quickly they must be applied
- Vendor access: No defined process for granting or revoking remote access
According to the U.S. Department of Energy, retrofitting cybersecurity controls can cost 5-10 times more than incorporating them during initial design and construction.
Building owners who get this right are embedding cybersecurity requirements into:
- Design standards: Functional specifications that require network segmentation, secure remote access, and encrypted communications
- Procurement language: Contract clauses that define password policies, patching timelines, and access control procedures
- Vendor selection: Evaluation criteria that include cybersecurity capabilities and support
One example: requiring all vendors to use a centralized, zero-trust remote access platform rather than allowing each vendor to create their own VPN or port forwarding rule. This single design decision dramatically reduces attack surface while improving visibility and control.
The bottom line: retrofitting cybersecurity always costs more than designing for it from the start.
Vulnerability Overload: What Owners Should Actually Worry About
After implementing asset discovery tools, many building owners receive reports listing 15,000+ vulnerabilities across their portfolio. The reaction is usually panic followed by paralysis. Where do you even start?
Osman Saleem calls this problem "enumerating badness"—an endless game of whack-a-mole that rarely addresses the actual risk. The smarter approach is to reframe the problem entirely.
"You don't have to fix everything," Saleem explained at NexusCon. "Focus on what matters—now, next, never."
This triage model helps owners prioritize vulnerabilities based on actual risk rather than theoretical computer vulnerability scoring system scores:
Now: High-risk, exploitable vulnerabilities with known attack vectors
- Internet-facing systems with critical vulnerabilities
- Default credentials on access control systems
- Unpatched systems with active exploits
Next: Items that need scheduled remediation but don't pose immediate risk
- Vulnerabilities in systems that are network-segmented
- Software that's end-of-life but not internet-facing
- Configuration issues that can be addressed during regular maintenance
Never: Low-consequence issues that won't affect operations
- Theoretical vulnerabilities on isolated systems
- Issues that require physical access to exploit
- Known vulnerabilities on systems scheduled for replacement
The key is coupling this prioritization with governance. Building owners need to:
- Define risk thresholds: What level of risk is acceptable for which types of systems?
- Assign ownership: Who's responsible for remediation in each category?
- Establish timelines: When must "Now" issues be fixed?
- Test preparedness: Run tabletop exercises to validate response plans
Saleem also recommends linking vulnerability remediation to capital project timelines. If an HVAC system needs a major upgrade in two years, it may not make sense to invest heavily in patching its current control system. Instead, ensure the replacement system meets current security standards.
Both the NIST SP 800-82 framework and the IEC 62443 standard support this risk-based approach. NIST focuses on probability times impact for general risk assessment. IEC 62443 emphasizes consequence-based planning for mission-critical systems where failure could result in injury, environmental damage, or critical infrastructure disruption.
The goal isn't perfection—it's pragmatic risk management aligned with business objectives.
What Everyone's Seeing: Common Patterns Across the Industry
Despite coming from different corners of the industry—integrators, consultants, owners, and technology providers—the NexusCon presenters kept circling back to the same problems.
Port forwarding showed up in every presentation. It's the convenient shortcut that punches holes in your firewall so vendors can remotely access building systems. It's also the entry point for most attacks. Joe Gaspardone from Montgomery Technologies has seen it repeatedly: systems that got hacked all had port forwarding enabled. Tom Balme from Lendlease made eliminating port forwarding a primary goal of their security program. The message was unanimous: stop doing this.
Nobody owns the problem. IT thinks facilities has it. Facilities thinks IT has it. Vendors assume the owner is managing it. Michael MacMahon from Newcomb & Boyd put it bluntly: "There's too much trust in this industry. Everyone assumes someone else has it handled. Nobody does."
The "air gap" myth keeps getting people hurt. Multiple presenters shared stories of supposedly isolated systems getting infected. An engineer plugs in a thumb drive. A contractor brings in a laptop. Suddenly your "air-gapped" BMS is encrypting every controller in the building. The cost to recover? One example ran over $200,000.
Vulnerability lists are overwhelming and mostly useless. Osman Saleem from Actimeta sees building owners receive reports listing 15,000+ vulnerabilities and freeze. They don't know where to start, so they don't start at all. The solution isn't ignoring the problem—it's triaging ruthlessly based on actual risk rather than theoretical CVSS scores.
Construction and operations teams don't talk. MacMahon highlighted the disconnect: "The hardest part is that construction and operations teams never talk—the facility group inherits the mess." When cybersecurity isn't embedded in design standards from the beginning, fixing it later costs 5-10 times more.
But the presenters also showed what works:
Start with remote access. Lendlease didn't begin with a massive audit. They secured remote access first—closing the most common attack vector immediately. The results came fast: 19 assets in six months, with immediate risk reduction and visible ROI that unlocked budget for the next phases.
Triage vulnerabilities into "now, next, never." Saleem's framework gives owners a practical way to prioritize thousands of findings without panic or paralysis.
Embed security in design standards. The owners who require network segmentation, secure remote access, and clear vendor security protocols from day one avoid the expensive retrofitting cycle.
Test your response plans. Multiple presenters emphasized tabletop exercises—not just having an incident response plan, but actually practicing it with the people who'd need to execute it.
The common thread? Stop assuming someone else has it covered. Start with one high-impact change. Prove the value. Scale from there.

The Market Is Moving: From Liability to Expectation
For years, building owners could ignore OT cybersecurity because tenants didn't ask about it, insurance companies didn't require it, and regulations didn't mandate it. That's changing fast.
Tom Balme from Lendlease shared a watershed moment: "We got our first lease requirement asking what we'd done for OT cyber before they'd sign."
This isn't isolated. Sophisticated tenants—particularly financial services firms, healthcare organizations, and technology companies—are beginning to include cybersecurity provisions in lease negotiations. They want to know:
- How is the building's OT network secured?
- Who has remote access to building systems?
- What monitoring and incident response capabilities exist?
- What happens if there's a breach?
According to CBRE research, 41% of corporate tenants now consider cybersecurity practices when evaluating office space, up from 18% in 2022.
Joe Gaspardone notes the ripple effect: "When tenants start asking for it, the rest of the market follows."
Beyond tenant pressure, other forces are accelerating adoption:
Insurance Requirements: Cyber insurance carriers are tightening requirements, with some explicitly asking about OT security controls before providing coverage or competitive rates.
ESG Expectations: Environmental, Social, and Governance (ESG) frameworks increasingly include cybersecurity and data protection as material risk factors.
Regulatory Momentum: While building-specific OT regulations remain limited, frameworks like IEC 62443 and NIST SP 800-82 are establishing baseline expectations for critical infrastructure.
Reputational Risk: News of a building cyberattack spreads quickly, damaging not only the immediate asset but the owner's brand across their portfolio.
The competitive dynamic is clear: proactive building owners who can demonstrate robust OT cybersecurity practices gain an advantage in lease negotiations, insurance renewals, and capital raising. Those who can't are starting to pay a premium—in both literal costs and lost opportunities.
From Horror to Habit: A Playbook for Building Owners
The horror stories are real. The risks are material. But the path forward doesn't require an army of cybersecurity experts or unlimited budget. It requires systematic thinking and disciplined execution.
Here's the practical checklist for building owners:
1. Know what's connected
- Inventory all OT systems and devices
- Map who has remote access to what
- Document network architecture
2. Control who accesses it
- Implement zero-trust remote access for all vendors
- Eliminate port forwarding and legacy VPNs
- Enforce multi-factor authentication
- Regularly audit user accounts and permissions
3. Document roles and risk thresholds
- Assign clear ownership for OT cybersecurity
- Define acceptable risk levels for different system types
- Establish escalation procedures for incidents
4. Update contracts with cyber clauses
- Include cybersecurity requirements in vendor contracts
- Specify patching timelines and responsibilities
- Require security training for vendor staff
- Define liability and insurance requirements
5. Design security into new builds
- Embed cybersecurity in functional design standards
- Require network segmentation by default
- Specify secure-by-design equipment in procurement
- Include OT security in commissioning checklists
6. Test response plans annually
- Conduct tabletop exercises with key stakeholders
- Validate backup and recovery procedures
- Update incident response plans based on lessons learned
- Practice communication protocols with tenants and regulators
The goal isn't to eliminate all risk—that's impossible with legacy systems and mixed-vintage equipment. The goal is to know where your walls are, who holds the keys, and ensure you never assume someone else locked the door.
The Real Choice
Building owners face a choice, but it's not the one they think. The choice isn't whether to address OT cybersecurity—the market is making that decision for you. The choice is whether to act strategically or reactively.
Strategic action means:
- Starting with high-impact, quick-win initiatives like securing remote access
- Building governance structures that establish clear ownership
- Incorporating security into design standards for future projects
- Prioritizing vulnerabilities based on actual risk, not theoretical scores
- Testing your preparedness through regular exercises
Reactive action means:
- Paying ransoms or six-figure remediation costs after an incident
- Losing tenants who cite security concerns
- Facing legal liability for preventable breaches
- Playing catch-up while competitors establish security as a differentiator
The building owners who move first—like Lendlease—aren't just protecting their assets. They're positioning them for a market where cybersecurity is becoming a leasing differentiator, an ESG requirement, and a competitive advantage.
Want to learn more about securing your building portfolio? Join the conversation in the Nexus Pro community, where building owners and operators share practical strategies for OT cybersecurity.
About This Article: This article is based on the "Under Siege: Cyber Security Horror & Success Stories" session at NexusCon 2024, featuring presentations from Joe Gaspardone (Montgomery Technologies), Michael MacMahon (Newcomb & Boyd), Joe Aamidor (Aamidor Consulting), Tom Balme (Lendlease), Cory Clarke (Neeve), and Osman Saleem (Actimeta).
A ransomware attack locked tenants out of a commercial office building for three days. Four major tenants cited the incident when they didn't renew their leases. The financial hit? Over $2 million in losses and litigation. This happened to a real building, and stories like it are becoming common enough that savvy tenants now ask about OT security before signing leases.
These stories—and practical solutions—came from a recent NexusCon session where building owners, consultants, and technology providers gathered to talk about what's actually happening in the field. The news isn't all bad. Lendlease successfully secured 19 buildings covering 1.1 million square feet in under six months. Actimeta has developed frameworks for triaging thousands of vulnerabilities into manageable priorities. And multiple owners shared practical steps that work without requiring unlimited budgets or armies of cybersecurity experts.
This article covers both the horror stories and the playbook for fixing them.
The Wake-Up Call: When Smart Buildings Get Dumb
It's 4 a.m. The first office worker arrives at the building entrance. The door won't unlock. By 6 a.m., there's a line stretching down the block.
The access control system has been ransomwared.
The property management company gets the emergency call around 6:30. By 9 a.m., the building owner is staring at an impossible choice: pay $7,200 in Bitcoin to criminals, or pay $65,000 to their vendor—plus burn countless staff hours—rebuilding the system from scratch.
This story comes from Joe Gaspardone, COO at Montgomery Technologies, who's spent 15 years turning tangled building networks into secure, organized systems. He's seen this scenario play out multiple times. The access control incident? Four major tenants left when their leases ended, and they specifically mentioned the hack as a reason they didn't renew.

Worse stories exist. An air-gapped BMS—supposedly unhackable because it had no internet connection—got infected when an engineer plugged in a thumb drive. No internet meant no alerts. The malware spread to every controller, burrowing into device firmware. Cost to fix: $200,000 to rip out, replace, and restore. Plus significant rent credits to tenants who suffered through days of comfort issues.
Elevators have been ransomwared. Multiple times.
Lobby directories have displayed pornography until someone physically disconnected them. Cost to remediate: $7,400.
Security cameras got quietly hacked and accessed for months. Two cases of identity theft followed. Eventually the system got ransomwared too: pay $19,700 in Bitcoin or $180,000 to the vendor.
Building systems aren't theoretical targets anymore. They're getting hit. And the old assumptions about being protected—air gaps, obscurity, 'we're too small to matter'—no longer hold.
The Hidden Cost of Convenience
Your HVAC contractor needs remote access to troubleshoot a problem at 11 p.m. Your elevator vendor needs to push a software update. Your tenant wants seamless badge access integrated with their corporate systems.
Every reasonable request opens a door.
The habits that keep buildings running—port forwarding to let vendors in, shared login credentials, default passwords nobody bothered changing—create exposure. Port forwarding is particularly dangerous. It punches a hole through your firewall, creating a direct pathway from the internet to your building systems.

Michael MacMahon, an OT security consultant at Newcomb & Boyd, has watched this pattern repeat: "There's too much trust in this industry. Everyone assumes someone else has it handled. Nobody does."
Here's a test: Who manages the cameras in your building? Who owns the Wi-Fi in your amenity spaces? Who's accountable when the BMS vendor's laptop brings in malware?
In most buildings, the answers are unclear. IT assumes facilities is handling it. Facilities assumes IT has it covered. Vendors assume the owner is managing security. Joe Aamidor, who consults with owners on building technology strategy, describes the result: "The awareness starts at the board, and they think it's covered—until they realize no one actually owns OT."
One building found out their amenity Wi-Fi was being used for illegal activity when the ISP flagged them. Then the FBI sent a letter: "As the owner of this IP address, you may be liable." The activity involved child trafficking. Nobody had set up even basic security on the network because nobody thought it was their job.
Convenience isn't free. It trades security for efficiency. The problem is that most building owners don't realize they're making that trade until something breaks.
The Myth of "We're Covered"
"Our IT team handles that."
This might be the most dangerous sentence in commercial real estate.
Building systems—HVAC, elevators, access control, lighting—usually sit outside IT's visibility. They're managed by facilities staff or vendors. They run on separate networks. They use protocols IT staff don't understand. And IT security tools often can't even see them, let alone protect them.
Picture a typical building:
- HVAC: Managed by a mechanical contractor with their own remote access
- Access control: Run by a security vendor on a separate network
- Elevators: Maintained by an elevator company using proprietary systems
- Cameras: Operated by yet another vendor
Each system has different remote access methods. Each vendor follows different security practices—or none. Each connection is a potential entry point.
Research from Claroty found that 78% of organizations have separate OT and IT security teams that don't coordinate well. The blind spots this creates are significant.
What gets lost in this fragmentation is accountability. Who's responsible when something goes wrong? Who should be tracking vulnerabilities? Who decides what level of risk is acceptable?
Those questions matter more than any security tool you can buy. Until you answer them, you're just adding more technology to an already confusing mess.
A Real Fix: The Lendlease OT Cyber Journey
When Lendlease decided to address OT cybersecurity across their portfolio, they didn't start with a massive audit that would identify thousands of vulnerabilities. They started with the most exposed point: remote access.
Tom Balme, who leads building technology strategy for Lendlease's investment portfolio, explains the thinking: "An audit will tell you to secure your internet-facing systems first—so don't wait to be told. Start there."
Lendlease developed a phased approach aligned with the NIST Cybersecurity Framework:
Phase 1 (FY25): Protect — Implement secure remote access across the portfolio
Phase 2 (FY26): Identify — Conduct OT audits and deploy asset discovery and vulnerability assessment tools
Phase 3 (FY27): Detect, Respond, Recover — Add monitoring, incident response capabilities, and backup systems

Why start with protection rather than identification? Because it delivers the fastest risk reduction. Securing remote access immediately closes the most common attack vector—without requiring a lengthy audit process or remediation of thousands of vulnerabilities.
The results speak for themselves:
- 19 buildings secured in less than six months
- 125 OT systems protected
- 770+ users onboarded (a mix of facilities staff, contractors, and tenants)
- Immediate cyber uplift delivered
Perhaps most importantly, the project eliminated legacy VPNs and port forwarding—the swiss cheese in most building networks—and gave Lendlease visibility and control over who accesses their OT environments.
Cory Clarke, CPO at Neeve (the platform Lendlease used), notes that the approach allowed rapid deployment: "Simple setup meant the team could start deploying within weeks. Self-service web-based remote access made it practical at scale."
One of the bigger challenges? Tenants. Of the 770+ users onboarded, 355 were tenants who needed access to systems they'd installed in their leased spaces. Getting tenant buy-in and managing their access required clear communication about why the changes mattered and how the new system would work.

Another challenge: port forwarding. Many vendors had grown accustomed to this convenient but dangerous practice. Balancing security requirements with vendor pushback on changing established workflows required patience and clear explanation of the risks.
But the biggest lesson? Starting small and showing results unlocked funding and board buy-in. By proving value quickly, Lendlease secured investment for the next phases of their program.
Tom Balme's advice for other owners: "Start with one building. Prove the value. Scale from there."
Designing for Security: Don't Bolt It On Later
One of the most expensive mistakes building owners make is treating cybersecurity as an afterthought. The conversation between Osman Saleem, Principal Consultant at Actimeta, and Michael MacMahon during the NexusCon session highlighted a critical disconnect: construction teams and operations teams rarely talk to each other during the design phase.
"The hardest part is that construction and operations teams never talk—the facility group inherits the mess," MacMahon explained.
When cybersecurity isn't embedded in design standards and procurement specifications, the cost and complexity of retrofitting security controls later multiplies. Consider these common scenarios:
- Default passwords: Systems ship with factory defaults that never get changed
- Flat networks: All building systems share a single network with no segmentation
- No patching protocols: Contracts don't specify who's responsible for software updates or how quickly they must be applied
- Vendor access: No defined process for granting or revoking remote access
According to the U.S. Department of Energy, retrofitting cybersecurity controls can cost 5-10 times more than incorporating them during initial design and construction.
Building owners who get this right are embedding cybersecurity requirements into:
- Design standards: Functional specifications that require network segmentation, secure remote access, and encrypted communications
- Procurement language: Contract clauses that define password policies, patching timelines, and access control procedures
- Vendor selection: Evaluation criteria that include cybersecurity capabilities and support
One example: requiring all vendors to use a centralized, zero-trust remote access platform rather than allowing each vendor to create their own VPN or port forwarding rule. This single design decision dramatically reduces attack surface while improving visibility and control.
The bottom line: retrofitting cybersecurity always costs more than designing for it from the start.
Vulnerability Overload: What Owners Should Actually Worry About
After implementing asset discovery tools, many building owners receive reports listing 15,000+ vulnerabilities across their portfolio. The reaction is usually panic followed by paralysis. Where do you even start?
Osman Saleem calls this problem "enumerating badness"—an endless game of whack-a-mole that rarely addresses the actual risk. The smarter approach is to reframe the problem entirely.
"You don't have to fix everything," Saleem explained at NexusCon. "Focus on what matters—now, next, never."
This triage model helps owners prioritize vulnerabilities based on actual risk rather than theoretical computer vulnerability scoring system scores:
Now: High-risk, exploitable vulnerabilities with known attack vectors
- Internet-facing systems with critical vulnerabilities
- Default credentials on access control systems
- Unpatched systems with active exploits
Next: Items that need scheduled remediation but don't pose immediate risk
- Vulnerabilities in systems that are network-segmented
- Software that's end-of-life but not internet-facing
- Configuration issues that can be addressed during regular maintenance
Never: Low-consequence issues that won't affect operations
- Theoretical vulnerabilities on isolated systems
- Issues that require physical access to exploit
- Known vulnerabilities on systems scheduled for replacement
The key is coupling this prioritization with governance. Building owners need to:
- Define risk thresholds: What level of risk is acceptable for which types of systems?
- Assign ownership: Who's responsible for remediation in each category?
- Establish timelines: When must "Now" issues be fixed?
- Test preparedness: Run tabletop exercises to validate response plans
Saleem also recommends linking vulnerability remediation to capital project timelines. If an HVAC system needs a major upgrade in two years, it may not make sense to invest heavily in patching its current control system. Instead, ensure the replacement system meets current security standards.
Both the NIST SP 800-82 framework and the IEC 62443 standard support this risk-based approach. NIST focuses on probability times impact for general risk assessment. IEC 62443 emphasizes consequence-based planning for mission-critical systems where failure could result in injury, environmental damage, or critical infrastructure disruption.
The goal isn't perfection—it's pragmatic risk management aligned with business objectives.
What Everyone's Seeing: Common Patterns Across the Industry
Despite coming from different corners of the industry—integrators, consultants, owners, and technology providers—the NexusCon presenters kept circling back to the same problems.
Port forwarding showed up in every presentation. It's the convenient shortcut that punches holes in your firewall so vendors can remotely access building systems. It's also the entry point for most attacks. Joe Gaspardone from Montgomery Technologies has seen it repeatedly: systems that got hacked all had port forwarding enabled. Tom Balme from Lendlease made eliminating port forwarding a primary goal of their security program. The message was unanimous: stop doing this.
Nobody owns the problem. IT thinks facilities has it. Facilities thinks IT has it. Vendors assume the owner is managing it. Michael MacMahon from Newcomb & Boyd put it bluntly: "There's too much trust in this industry. Everyone assumes someone else has it handled. Nobody does."
The "air gap" myth keeps getting people hurt. Multiple presenters shared stories of supposedly isolated systems getting infected. An engineer plugs in a thumb drive. A contractor brings in a laptop. Suddenly your "air-gapped" BMS is encrypting every controller in the building. The cost to recover? One example ran over $200,000.
Vulnerability lists are overwhelming and mostly useless. Osman Saleem from Actimeta sees building owners receive reports listing 15,000+ vulnerabilities and freeze. They don't know where to start, so they don't start at all. The solution isn't ignoring the problem—it's triaging ruthlessly based on actual risk rather than theoretical CVSS scores.
Construction and operations teams don't talk. MacMahon highlighted the disconnect: "The hardest part is that construction and operations teams never talk—the facility group inherits the mess." When cybersecurity isn't embedded in design standards from the beginning, fixing it later costs 5-10 times more.
But the presenters also showed what works:
Start with remote access. Lendlease didn't begin with a massive audit. They secured remote access first—closing the most common attack vector immediately. The results came fast: 19 assets in six months, with immediate risk reduction and visible ROI that unlocked budget for the next phases.
Triage vulnerabilities into "now, next, never." Saleem's framework gives owners a practical way to prioritize thousands of findings without panic or paralysis.
Embed security in design standards. The owners who require network segmentation, secure remote access, and clear vendor security protocols from day one avoid the expensive retrofitting cycle.
Test your response plans. Multiple presenters emphasized tabletop exercises—not just having an incident response plan, but actually practicing it with the people who'd need to execute it.
The common thread? Stop assuming someone else has it covered. Start with one high-impact change. Prove the value. Scale from there.

The Market Is Moving: From Liability to Expectation
For years, building owners could ignore OT cybersecurity because tenants didn't ask about it, insurance companies didn't require it, and regulations didn't mandate it. That's changing fast.
Tom Balme from Lendlease shared a watershed moment: "We got our first lease requirement asking what we'd done for OT cyber before they'd sign."
This isn't isolated. Sophisticated tenants—particularly financial services firms, healthcare organizations, and technology companies—are beginning to include cybersecurity provisions in lease negotiations. They want to know:
- How is the building's OT network secured?
- Who has remote access to building systems?
- What monitoring and incident response capabilities exist?
- What happens if there's a breach?
According to CBRE research, 41% of corporate tenants now consider cybersecurity practices when evaluating office space, up from 18% in 2022.
Joe Gaspardone notes the ripple effect: "When tenants start asking for it, the rest of the market follows."
Beyond tenant pressure, other forces are accelerating adoption:
Insurance Requirements: Cyber insurance carriers are tightening requirements, with some explicitly asking about OT security controls before providing coverage or competitive rates.
ESG Expectations: Environmental, Social, and Governance (ESG) frameworks increasingly include cybersecurity and data protection as material risk factors.
Regulatory Momentum: While building-specific OT regulations remain limited, frameworks like IEC 62443 and NIST SP 800-82 are establishing baseline expectations for critical infrastructure.
Reputational Risk: News of a building cyberattack spreads quickly, damaging not only the immediate asset but the owner's brand across their portfolio.
The competitive dynamic is clear: proactive building owners who can demonstrate robust OT cybersecurity practices gain an advantage in lease negotiations, insurance renewals, and capital raising. Those who can't are starting to pay a premium—in both literal costs and lost opportunities.
From Horror to Habit: A Playbook for Building Owners
The horror stories are real. The risks are material. But the path forward doesn't require an army of cybersecurity experts or unlimited budget. It requires systematic thinking and disciplined execution.
Here's the practical checklist for building owners:

1. Know what's connected
- Inventory all OT systems and devices
- Map who has remote access to what
- Document network architecture
2. Control who accesses it
- Implement zero-trust remote access for all vendors
- Eliminate port forwarding and legacy VPNs
- Enforce multi-factor authentication
- Regularly audit user accounts and permissions
3. Document roles and risk thresholds
- Assign clear ownership for OT cybersecurity
- Define acceptable risk levels for different system types
- Establish escalation procedures for incidents
4. Update contracts with cyber clauses
- Include cybersecurity requirements in vendor contracts
- Specify patching timelines and responsibilities
- Require security training for vendor staff
- Define liability and insurance requirements
5. Design security into new builds
- Embed cybersecurity in functional design standards
- Require network segmentation by default
- Specify secure-by-design equipment in procurement
- Include OT security in commissioning checklists
6. Test response plans annually
- Conduct tabletop exercises with key stakeholders
- Validate backup and recovery procedures
- Update incident response plans based on lessons learned
- Practice communication protocols with tenants and regulators
The goal isn't to eliminate all risk—that's impossible with legacy systems and mixed-vintage equipment. The goal is to know where your walls are, who holds the keys, and ensure you never assume someone else locked the door.
The Real Choice
Building owners face a choice, but it's not the one they think. The choice isn't whether to address OT cybersecurity—the market is making that decision for you. The choice is whether to act strategically or reactively.
Strategic action means:
- Starting with high-impact, quick-win initiatives like securing remote access
- Building governance structures that establish clear ownership
- Incorporating security into design standards for future projects
- Prioritizing vulnerabilities based on actual risk, not theoretical scores
- Testing your preparedness through regular exercises
Reactive action means:
- Paying ransoms or six-figure remediation costs after an incident
- Losing tenants who cite security concerns
- Facing legal liability for preventable breaches
- Playing catch-up while competitors establish security as a differentiator
The building owners who move first—like Lendlease—aren't just protecting their assets. They're positioning them for a market where cybersecurity is becoming a leasing differentiator, an ESG requirement, and a competitive advantage.
Want to learn more about securing your building portfolio? Join the conversation in the Nexus Pro community, where building owners and operators share practical strategies for OT cybersecurity.
About This Article: This article is based on the "Under Siege: Cyber Security Horror & Success Stories" session at NexusCon 2024, featuring presentations from Joe Gaspardone (Montgomery Technologies), Michael MacMahon (Newcomb & Boyd), Joe Aamidor (Aamidor Consulting), Tom Balme (Lendlease), Cory Clarke (Neeve), and Osman Saleem (Actimeta).




This is a great piece!
I agree.